German police recently busted a €100 million scam operated by a Bulgarian-based crime group posing as a legitimate online broker. The fraudsters created online trading platforms for complex financial instruments, assuring clients that the investments were safe and major losses would be insured.
Victims were shown impressive but fake earnings results to encourage additional deposits into their online accounts. In the case of losses, they were encouraged to make additional investments to cover the losses.
The network funneled the proceeds into shell companies that laundered the money. The group operated call centers and social media sites to lure its victims.
The increasing phenomenon of cybertheft is exacerbated by the growing involvement of organized crime. Many financial losses have been traced back to the bank accounts of specific criminal organizations, especially in Russia and former Soviet bloc countries in Eastern Europe, such as Bulgaria.
These tech-savvy gangsters won’t whack you; they’ll hack you.
The prevalence of financial rip-offs has reached epidemic proportions. According to a recent study conducted by the National Center for Victims of Crime and the Financial Industry Regulatory Authority (FINRA), about $50 billion is lost annually in the United States from schemes that defraud individuals.
The highest losses from these financial crimes every year occur under the category of investment fraud (see chart, compiled with data from the two organizations):
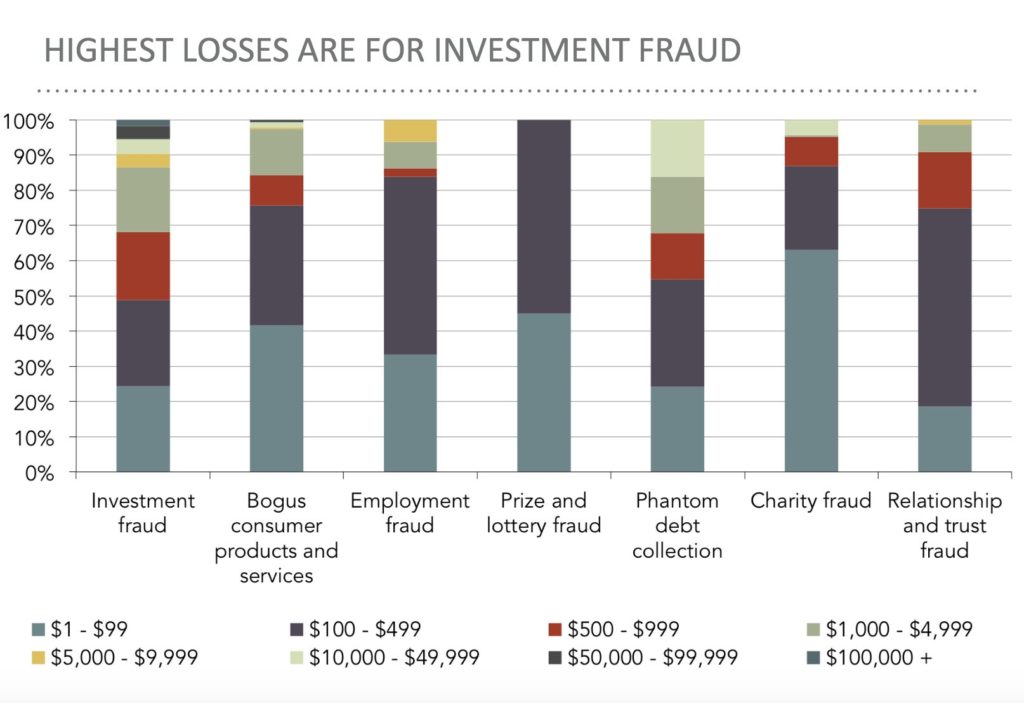
How to Avoid the Traps
To prevent getting ripped off by a cybercrook, consider these 12 precautionary steps:
1) Clean up your social media practices by not “friending” or connecting with unknown people.2) Don’t click unknown web sites that have appeared in your inbox via unsolicited emails.
2) Avoid using debit cards online. Credit card companies enforce fraud control and restitution; you can usually get your money back if you’ve been a victim of cyber crime. But if hackers access your checking account via a debit card, the money is usually gone forever with no hope of redress.
3) Strengthen password protection. Don’t use family names or personal biographical data that can be deduced or unearthed.
4) Use security software, made by major anti-hacking companies such as Cisco Systems (NSDQ: CSCO), Symantec (NSDQ: SYMC) and FireEye (NSDQ: FEYE).
5) Never respond to Internet ads for anti-spyware programs because they may actually open up spyware.
7) Don’t provide your birth date on your social media profiles. Doing so makes it easier to steal your identity. Also consider throwing potential cyberthieves off the scent, by listing an erroneous birthday date.
7) Beware messages about IRS refunds. Piquing interest by mentioning tax refunds is an increasingly common tactic used by cybercriminals to con people into opening a link or attachment associated with an unsolicited email. These emails take people to a fake page where thieves try to steal personal data.
The IRS recently issued a bulletin that warned of a new scam: criminals posing as debt collection agency officials acting at the behest of the IRS. These digital con artists contact taxpayers via email to say a refund was deposited in error. They ask the taxpayers to forward the money to their collection agency. Incredibly enough, thousands of people have already fallen for this scheme.
Keep this important point in mind at all times: The IRS never initiates contact with taxpayers by email, text messages or social media to request personal or financial information.
8) Before initiating any financial transactions online, determine whether the web site is encrypted or not.
Always look for two things: the extra “s” at the end of http in the URL address and the trusted security lock symbols.
When you’re on the web page that’s asking for your credit card information, the “http” flips over to “https” if it’s a secure site. A lock symbol simultaneously appears on the right side of the address bar or at the bottom left of your browser window.
9) Enable “cookies” on your browser only for web sites that are important to you and which require it. Cookies are details web sites store on your computer, including your browsing habits. The majority of these web sites keep this data to themselves, but cookies provide a means for hackers to steal your personal information.
10) Avoid WiFi “trojan horses.” We live in an interconnected extended enterprise. Smartphones, laptops, tablets, and other WiFi-capable devices automatically connect to frequently used networks. For example, if you work in a home office, your laptop will default to your local Internet provider. But don’t get too comfortable with this convenience.
There’s a common fraud whereby cybercrooks set up a WiFi network with one overriding purpose—to fool your device into plugging in. The addresses of these imposter sites can have fiendishly clever names, such as Yahoo Starbucks, to attract unwitting victims. Go to “settings” and periodically delete the networks that your devices automatically join. Get a fresh start by joining them for the “first” time. Full story at Investing Daily


